-
Make the Most of the Mac’s Videoconferencing Capabilities
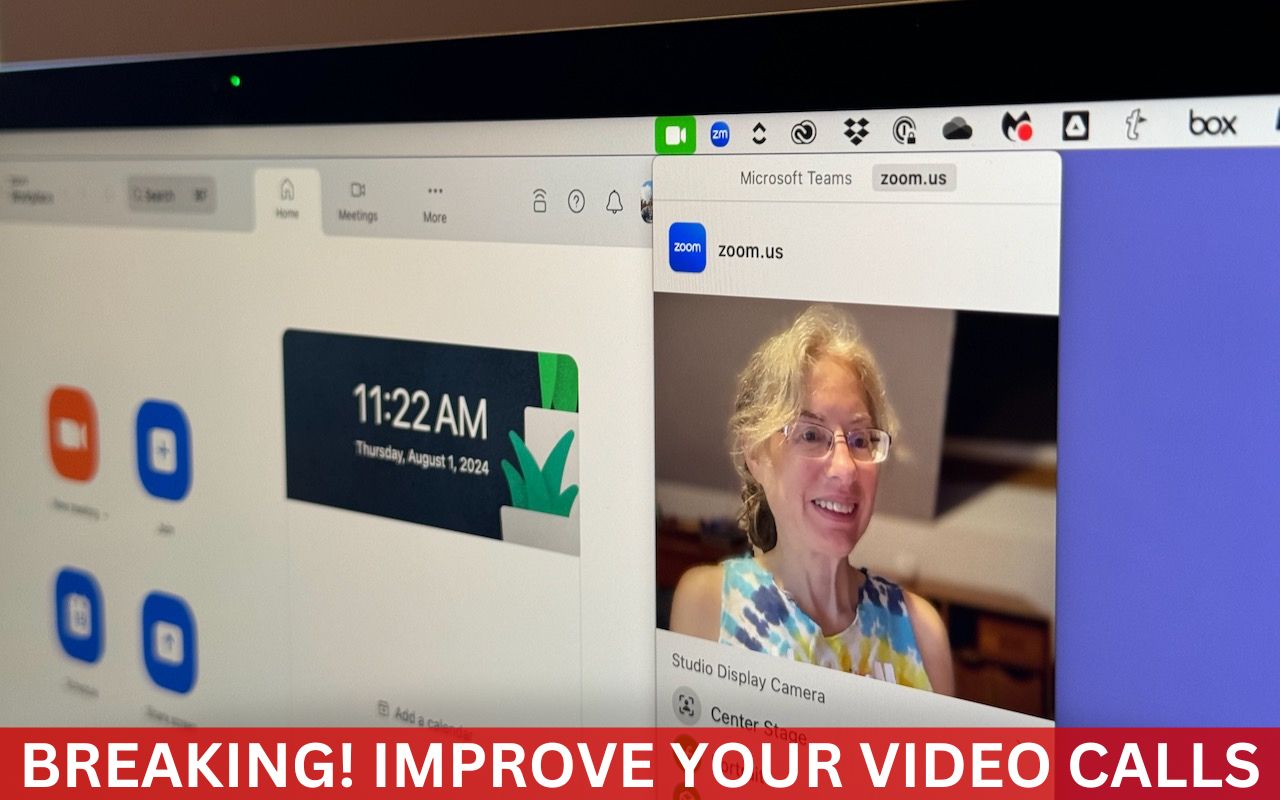
A side effect of the pandemic is that online videoconferencing improved drastically. Video calls happened before 2020, but videoconferencing wasn’t an everyday activity for most people. Now, with many people working remotely or in a hybrid model, it’s a fact of business life. To support videoconferencing tools, Apple has extended macOS’s basic webcam and microphone capabilities to allow Mac-pow... Read more -
Use High-Quality Cables for Optimal Performance and Safety
Apple’s prices for Thunderbolt, USB-C, and Lightning cables often seem unnecessarily high. $69 for a Read more -
When Should You “Ignore Ownership” on an External Drive?
Under the hood, macOS relies on Unix, which is a multi-user operating system. That’s why a Mac can host multiple users who, as long as they don’t know each other’s passwords, cannot see each other’s files. To maintain each user’s privacy, macOS relies on permissions that specify who can do what with any given file or folder. For the most part, permissions work how they’re supposed to, letting y... Read more -
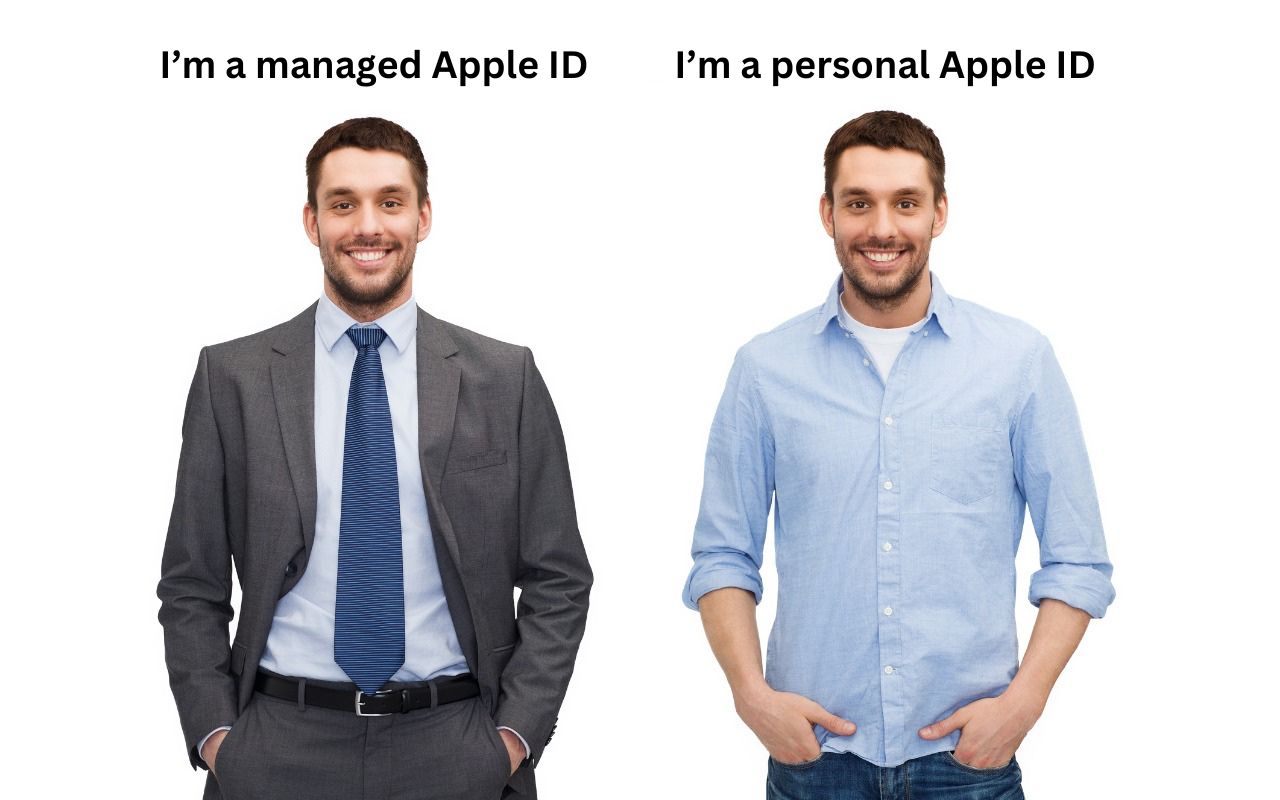
Understanding the Key Differences Between Personal and Managed Apple IDs
In the Apple world, the account that controls access to all your Apple-related online services is the Apple ID. Buying apps from the App Store, putting photos in iCloud Photos, and sharing data between iCloud-enabled apps—all these actions rely on your Apple ID. If you’re a regular Apple user, you have an Apple ID associated with your email address. Most Apple users set up an Apple ID when t... Read more -
Having Trouble with a Public Wi-Fi Network’s Captive Portal Login Page?
When you connect to a public Wi-Fi network at an airport, hotel, coffee shop, or school, you may need to interact with a captive portal login page to be granted access to the network. It might require you to enter login credentials, ask for your name, or make you agree to terms of service. But what if that login... Read more -
Missed an Alert? Check Notification Center
iOS, iPadOS, and macOS all let you specify whether any given app should show no notifications, temporary banners, or persistent alerts: look in Settings > Notifications and System Settings > Notifications. Temporary banners appear briefly and then automatically disappear, which is appropriate for notifications requiring no acknowledgment. But what if you see a temporary banner only as it’... Read more -
Protect Domains That Don’t Send Email from Email Spoofing
We recently wrote an article for those who manage their own Internet domain names about using SPF, DKIM, and DMARC to prevent your domains from being used in phishing attacks and enhance the deliverability of legitimate email. But what about other domains you own but don’t use for email? To make phishing attacks more believable, spammers sometimes forge email so it appears to come from parked d... Read more -
Be Careful When Scanning Unknown QR Codes
QR codes, those square, blocky codes you scan with your iPhone’s camera to load a Web page, have become ubiquitous. So much so that we seldom pause before scanning any QR code we see. But if you think about it, that’s the same as clicking random links in emails or texts, which is a terrible idea from a security perspective. “Quishing” (QR code phishing) isn’t commonplace yet, but some sources s... Read more